The smart Trick of Ransomware Protection That Nobody is Talking About
Wiki Article
How Rto can Save You Time, Stress, and Money.
Table of ContentsFascination About S3 Cloud BackupThe 2-Minute Rule for Protection Against RansomwareAn Unbiased View of Ransomware ProtectionGetting The Ransomware Protection To WorkThe Greatest Guide To Protection Against RansomwareSome Known Details About Ec2 Backup

International authorities have actually stepped in with regulatory compliance like General Data Protection Law (GDPR). The GDPR emphasizes the individual information legal rights of EU citizens, including the right to change, access, erase, or move their information. Individual information refers to any information that associates with a person. This includes names, physical characteristics, addresses, racial or ethnic qualities, and biometric information like DNA as well as fingerprints.
To maintain their data available in any way times, business require to maintain the IT framework energetic even in the instance of a catastrophe. This state of surefire access to information is referred to as data schedule. This short article reviews the fundamentals of information accessibility and its obstacles, and uses strategies to preserve a high degree of data accessibility.
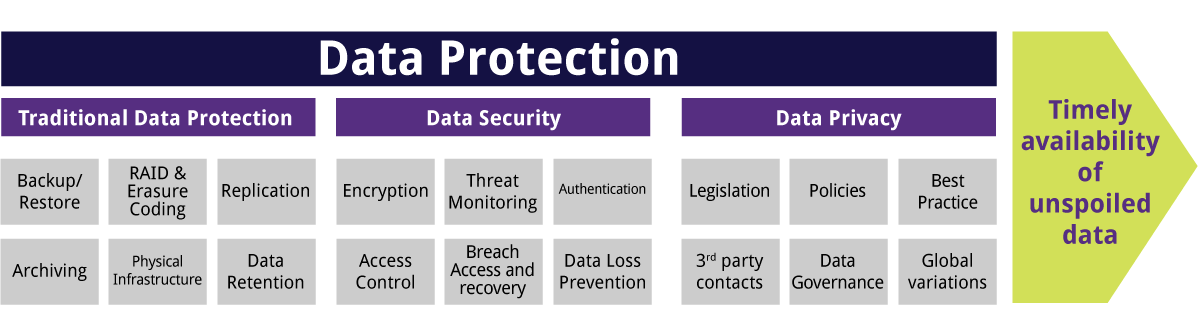
Without a proper information safety and security plan, sensitive details can come under the hands of assailants, allowing them to access to your network, and reveal the personal details of customers as well as staff members. This short article presents the concept of data protection and the various devices and approaches you can use to secure your information and stop a calamity.
Rumored Buzz on Data Protection
The encoded information can just be translated with an unique decryption trick. You can create the vital either at the time of security or in advance. File encryption makes sure the integrity of information by securing it from unauthorized adjustment. Encryption reduces the threat of accessing information from unreliable resources by verifying data's resource.A constant data defense system maintains a document of all data adjustments as well as enables you to recover a system to any type of previous factor in time. This sort of backup addresses the problem of losing data produced in between two set up backups. It likewise gives protection against assaults like ransomware or malware, as well as accidental deletion of data.
Any type of firm that processes as well as shops individual data of EU residents, also if it is not literally located in the EU, should put on the GDPR regulations. There are two major functions in the GDPR: the GDPR Data Cpu is an entity that holds or refines this kind of data in behalf of one more company, and also a GDPR Information Controller that accumulates or processes personal data for its own objectives.
Immutable S3 objects are safeguarded using things, or bucket-level arrangement of WORM as well as retention qualities. This performance offers both data defense, consisting of additional protection against unintended or harmful deletion as well as ransomware and also governing conformity.
S3 Cloud Backup for Dummies
Information defense is the process of protecting important info from corruption, concession or loss. The relevance of data protection boosts as the quantity of information developed as well as saved continues to expand at unprecedented rates. There is additionally little resistance for downtime that can make it difficult to access crucial details.
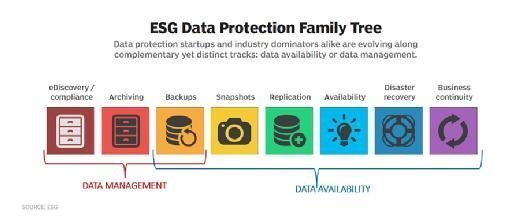
The crucial concepts of information defense are to protect as well as make readily available information under all circumstances. The term data security defines both the functional back-up of information along with business continuity/disaster recovery (BCDR). Data security methods are developing along 2 lines: information accessibility as well as information monitoring. Information schedule ensures users have the data they need to carry out company also if the information is harmed or lost.
Fascination About Ransomware Protection
Data lifecycle monitoring is the process of automating the activity of critical data to online and offline storage space. Information lifecycle administration is an extensive approach for valuing, cataloging and shielding info properties from application and customer errors, malware and also virus assaults, equipment failure or center outages as well as disturbances. Much more just recently, information management has actually involved include locating ways to unlock business value from otherwise inactive duplicates of information for reporting, test/dev enablement, analytics as well as various other purposes.(CDP) backs up all the information in a business whenever a change is made. Data portability-- the capability to move data amongst different application programs, calculating atmospheres or cloud services-- provides another collection of troubles and remedies for data defense.
The Main Principles Of S3 Backup
Information security is the process of securing crucial info from corruption, compromise or loss. anonymous The significance of data protection enhances as the amount of information developed and saved remains to expand at unmatched rates. There is also little tolerance for downtime that can make it difficult to accessibility vital info (https://packersmovers.activeboard.com/t67151553/how-to-connect-canon-mg3620-printer-to-computer/?ts=1667611228&direction=prev&page=last#lastPostAnchor).Safeguarding data from concession as well as guaranteeing information privacy are other crucial elements of information security. The coronavirus pandemic created countless employees to function from home, causing the requirement for remote data security. Businesses have to adapt to guarantee they are safeguarding information anywhere staff members are, from a central information center in the workplace to laptop computers in the house.
The essential concepts of information protection are to protect as well as make readily available information under all situations - https://calendly.com/clumi0/30min?month=2022-11.
Details lifecycle management is a detailed method for valuing, cataloging and also shielding info possessions from application and individual mistakes, malware and infection strikes, maker failure or center blackouts as well as disruptions. Extra lately, information management has actually come to include finding means to unlock business worth from otherwise inactive copies of information for reporting, test/dev enablement, analytics and various other objectives.
8 Simple Techniques For S3 Backup
(CDP) backs up all the data in a business whenever an adjustment is made. Information portability-- the ability to relocate data amongst various application programs, computing environments or cloud solutions-- presents another collection of troubles as well as options for data protection.Report this wiki page